Assignment 1: Task 1
The main advantage of Public-key cryptography over private-key
cryptography is that there is no need for a key exchange protocol
(there are issues of trust but we will discuss that later.) For each
party, there is a key generation algorithm that generates a
pair of keys (sk, pk). One of these keys, sk is the
secret key that is kept secret by the party while the other key, pk
is called a public key that is made public (by posting on one's
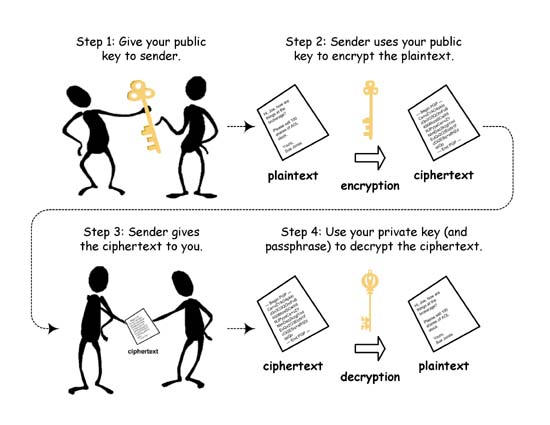
webpage for example). The following figure explains how the secret
communication happen using these keys in the public key model.
We would like to have secret communication amongst ourselves
(students registered in the course). Use GPG to generate a (secret key,
public key) pair for yourself and then let me know your public key
so that I may post this on the course website. You should use your
iitd email address and use 2048 bit RSA option while generating your
keys and the expiry should be sometime after the course ends. You
will be able to figure these things out by exploring the following
page for GPG from where you will also get the software:
http://www.gnupg.org
Here is the ascii version of my gpg
public key. You should save the ascii version of your public key in
a file named "<iitd-email-id>.asc", then encrypt this file
using my public key and then email this encrypted file to me with
the subject line "CSL759: public-key".
Note that this first task is important because I might want to send
your next task encrypted with your public key!